#[message.inboundProperties['http.headers']['X-Forwarded-For']]To Apply IP Blacklist
|
Where possible, we changed noninclusive terms to align with our company value of Equality. We maintained certain terms to avoid any effect on customer implementations. |
The IP blacklist policy can control whether a list or range of IP addresses can access and interact with a configured API endpoint. You use one of the following options to blacklist addresses for your API:
-
Option 1: Blacklist access based on the IP address of the request
-
Option 2: Blacklist access based on the origin IP address of the x-Forwarded-For header
Option 1: Blacklist access based on the IP address of the request
-
Click the version number of an API.
-
On the API dashboard, click Policies.
The list of any applied policies appears.
-
In Apply New Policy.
-
In Select Policy, choose IP Blacklist, and click Configure Policy.
-
Specify a list of IP addresses in the blacklist section of Apply IP Blacklist Policy.
Specified addresses are blacklisted to access and interact with your API.
You can specify an address or a range or addresses in the following ways:
-
Define a specific IP address by enumerating it in the white space. For example, 192.168.1.1.
-
Define a subset of addresses by identifying a subnet mask. For example, 192.168.3.1/30 will include the consolidated range: 192.168.3.0 - 192.168.3.3.
-
Define a whole range of IP addresses by stating the relevant octets of the IP address you want to permit. For example, setting
192.168will include IP addresses from 192.168.0.0 to 192.168.255.255.
Option 2: Blacklist access based on the origin IP address of the x-Forwarded-For header
If the client connects to your API through an HTTP proxy or a load-balancer, you can blacklist the client’s specific IP (the IP originating the request) instead of the address that will appear in the request. For example: Suppose you want to blacklist 192.168.2.3, the address of a client connecting through an HTTP proxy whose address is 92.40.1.255. The client requests appear with this public address. Typically, applications use the 'X-Forwarded-For' header to identify the origin IP addresses of a request that was redirected to your endpoint.
You can use a Mule expression to instruct the service to look for the IP address in the 'x-Forwarded-For' header:
Insert the IP address in the IP expression field:
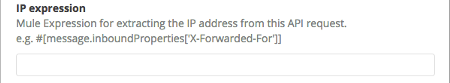
This instructs API Platform to look at the first IP address that ranks in the concatenated values of the 'x-Forwarded-For' header of the request.



