Studio Visual Editor
-
Add a global Signature message processor to your application, applying a unique Name for the element and keeping the default value,
JCE_SIGNER, in the Default Signer field (see image below, left). -
Click the JceSigner tab (see image below, right), then configure the message processor’s attributes according to the table below. Note that while none of the attributes on the Jce Signer tab are required, this global element is the only place you can define a Keystore Path and Keystore Password for your Signature element.
Field Req’d Value Reference or expression
If selected, in the Jce Signer Reference, use an expression to reference attributes you have defined elsewhere in the XML configuration of your applications, or to reference the configurations defined in a bean.
Define attributes
If selected, enter values in the following five fields.
Algorithm
Algorithm to encrypt the key, not required if using a keystore. Refer to Appendix for list of available algorithms.
Key
Unique key that encrypts and decrypts message; or, if using keystore, the name of the specific key within the keystore.
Keystore Path
Indicates the location (i.e. filepath) of the keystore file, required if using keystore.
Keystore Password
Password to access the keystore, required if using keystore.
Key Password
Password to read the key within the keystore; required only if the specific keys within the keystore have their own passwords.
If you are using a Keystore, you must also define a Key to specify which key within the keystore the application should invoke. The key can be configured either on the Global Element Properties window or in the Pattern Properties window.
+ * If configured in the Global Element Properties window, that key will be invoked for all message processors which refer to that global element — unless there is a different key specified in the local Pattern Properties window for that building block, because local configuration overrides global configurations. * If configured in the local Pattern Properties window, that key will be invoked only for that message processor, so any other message processors in the same flow that also refer to that global element would need a key configured in their Pattern Properties windows.
-
Add a Signature message processor to your flow.
-
Configure the message processor’s fields according to the table below.
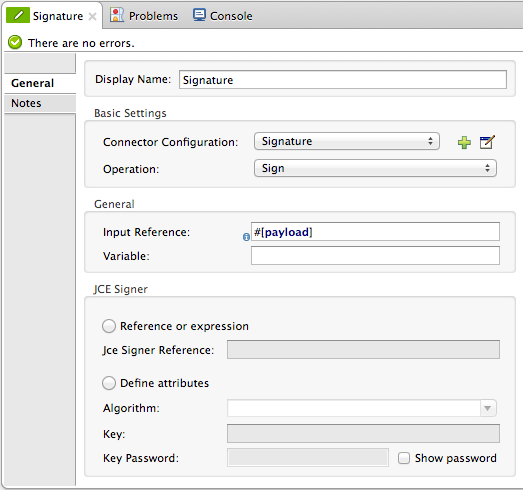
Field Req’d Value Display Name
x
A unique name for your message processor.
*Connector Configuration
*x
Use the name of the global element you created above.
Operation
x
Sign
Input Reference
Identify the part of the message payload to which you want to apply the signature. This value must be in byte array format. By default, Mule signs the entire message payload.
Variable
Indicate the location in which Mule should store the signature which enriches the message.
Reference or expression
If selected, in the Jce Signer Reference, use an expression to reference attributes you have defined elsewhere in the XML configuration of your applications, or to reference the configurations defined in a bean.
Define attributes
If selected, enter values in the following three fields.
Algorithm
Define an algorithm to encrypt the key, not required if using keystore.
Key
x
Unique key that encrypts and decrypts message; or, if using keystore, the name of the specific key within the keystore.
Key Password
Password to read the key within the keystore; required only if the specific keys within the keystore have their own passwords.
XML Editor or Standalone
-
Add a global
signature:configelement to your application, set above all the flows in your application. -
Configure the global element’s attributes and child element according to the table below. Note that while none of the attributes on the Jce Signer tab are required, this global element is the only place you can define a keystorePath and keystorePassword for your Signature element.
<signature:config name="Global_JCE_Signature" doc:name="Signature"> <signature:jce-signer-config algorithm="HmacMD5" key="1@s9bl>1LOJ94z4"/> </signature:config>Attribute Req’d Value name
x
A unique name for your global element.
doc:name
A display name for the element in Studio’s Visual Editor. Not applicable for Standalone.
Child Element Req’d signature:jce-signer-config
Child Element Attribute Req’d Value algorithm
Define an algorithm to encrypt the key, not required if using keystore. Refer to Appendix for list of available algorithms.
key
Unique key that encrypts and decrypts message; or, if using keystore, the name of the specific key within the keystore.
keystorePath
Indicates the location (i.e. filepath) of the keystore file, required if using keystore.
keystorePassword
Password to access the keystore, required if using keystore.
keyPassword
Password to read the key within the keystore; required only if the specific keys within the keystore have their own passwords.
If you are using a Keystore, you must also define a Key to specify which key within the keystore the application should invoke. The key can be configured either the global element window or in the element in your flow.
-
If configured in the global element, that key will be invoked for all message processors which refer to that global element — unless there is a different key specified in the local configuration for that element, because local configuration overrides global configurations.
-
If configured in the local element, that key will be invoked only for that element, so any other elements in the same flow that also refer to that global element would need a key configured in their local configurtions.
-
-
Add a
signature:signelement to your flow. -
Configure the element’s attributes and child element according to the tables below.
<signature:sign config-ref="Signature" doc:name="Signature"> <signature:jce-signer algorithm="HmacMD5" key="testing" keyPassword="passtestng"/> </signature:sign>Attribute Req’d Value config-ref
x
Use the name of the global element you created above.
doc:name
A display name for the element in Studio’s Visual Editor. Not applicable for Standalone.
input-ref
Identify the part of the message payload to which you want to apply the signature. This value must be in byte array format. By default, Mule signs the entire message payload.
variable
Indicate the location in which Mule should store the signature which enriches the message.
| Child Element | Req’d |
|---|---|
signature:jce-signer |
x |
| Child Element Attribute | Req’d | Value |
|---|---|---|
algorithm |
Define an algorithm to encrypt the key, not required if using keystore. |
|
key |
x |
Unique key that encrypts and decrypts message; or, if using keystore, the name of the specific key within the keystore. |
keyPassword |
Password to read the key within the keystore; required only if the specific keys within the keystore have their own passwords. |