Studio Visual Editor
-
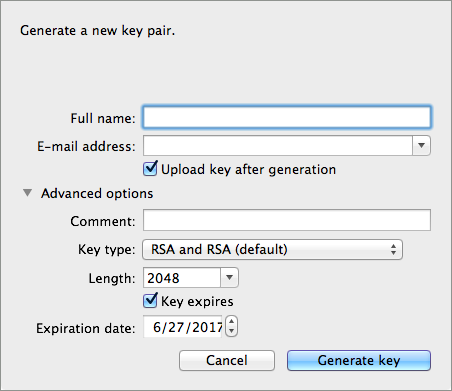
Use a tool such as GPG Keychain Access to import the other party’s public key. Refer to section below for more details about using GPG to facilitate implementation of PGP encryption and decryption in Mule.
-
Using the same tool, export the public key, selecting binary as the output format. This produces a key ring file with a
.gpgextension. -
Ensure that the
.gpgfile is stored in a place that the Mule application can access it at runtime; record the filepath of the.gpgfile (also known as your public key ring file). -
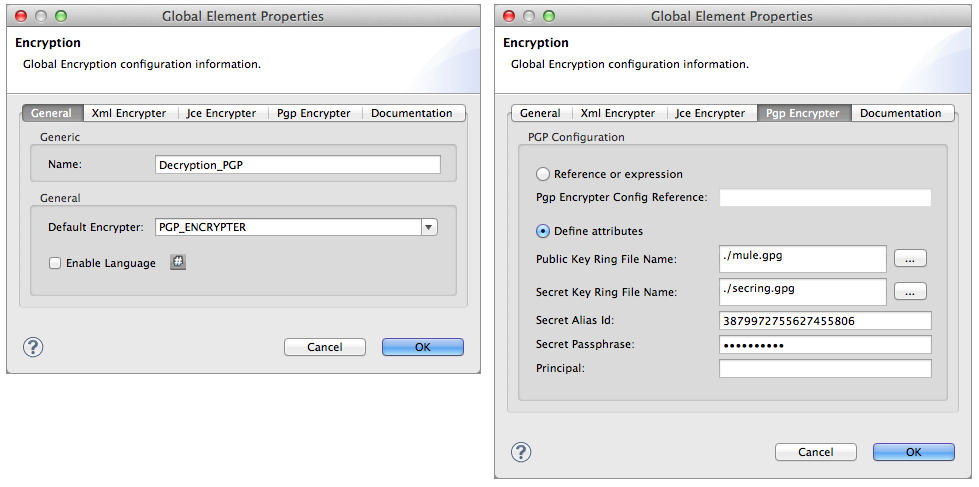
In your Mule application, create a global Encryption element, specifying a name for the element; change the default value for the Default Encrypter to
PGP_ENCRYPTER. -
On the Pgp Encrypter tab, configure the fields according to the table below.
Field Value General Tab
Name
Required - A unique name for the global element.
Default Encrypter
PGP_ENCRYPTER
Pgp Encrypter Tab
Reference or expression
If selected, in the Pgp Encrypter Config Reference, use an expression to reference attributes you have defined elsewhere in the XML configuration of your applications, or to reference the configurations defined in a bean.
Define attributes
If selected, enter values in the following field.
Public Key Ring File Name
Enter the filepath of the public key ring. This binary "key ring" holds the message receiver’s public key. Read more about creating the public key ring above. Note that you do not enter the public key itself, only the location of the key ring file in which the public is stored.
-
Set an Encryption message processor in the flow in which you wish to encrypt data in the message payload.
-
Configure the message processor according the table below.
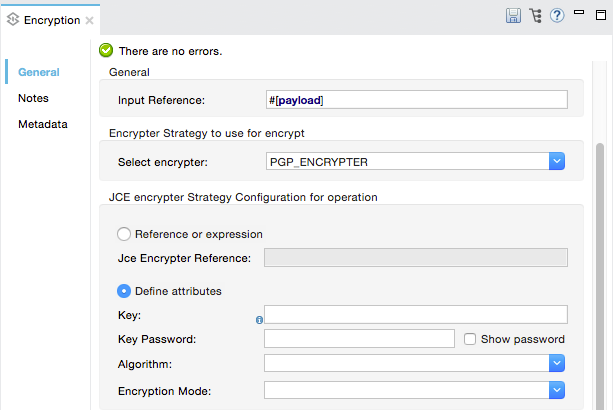
Field Value Display Name
A unique name for your message processor.
Config Reference
Required - Use the drop down to select the global Encryption element you created in the steps above.
Operation
Required - Encrypter
Input reference
Enter a Mule expression to define the part(s) of the message Mule should encrypt. If no value is entered, Mule encrypts the entire message payload.
Select encrypter
Required - PGP_ENCRYPTER
Reference or expression
If selected, in the Pgp Encrypter Reference, use an expression to reference attributes you have defined elsewhere in the XML configuration of your applications, or to reference the configurations defined in a bean.
Define attributes
If selected, enter values in the following field.
Principal
An alternative to using a clientID and secret to authenticate a client, define a username and password as the principal.
-
Click OK to save your PGP encrypter configuration.
XML Editor or Standalone
-
Use a tool such as GPG Keychain Access to import the other party’s public key.
-
Using the same tool, export the public key, selecting binary as the output format. This produces a key ring file with a
.gpgextension. -
Ensure that the
.gpgfile is stored in a place that the Mule application can access it at runtime; record the filepath of the.gpgfile (also known as your public key ring file). -
In your Mule application, create an global
encryption:configelement, set above all the flows in your config file. -
Configure the global element’s attributes and child element according to the table below.
<encryption:config name="Encryption_PGP" defaultEncrypter="PGP_ENCRYPTER" doc:name="Encryption_PGP"> <encryption:pgp-encrypter-config publicKeyRingFileName="./mule.gpg"/> </encryption:config>Attribute Value name
Required - A unique name for your global element.
defaultEncrypter
Required - PGP_ENCRYPTER
doc:name
A display name for the element in Studio’s Visual Editor. Not applicable for Standalone.
-
Child Element: Required -
encryption:pgp-encrypter-config -
Child Element Attribute: publicKeyRingFileName - Required - Set the value to the filepath of the public key ring. This binary "key ring" holds the message receiver’s public key. Read more about creating the public key ring above. Note that you do not enter the public key itself, only the location of the key ring file in which the public is stored.
-
-
To the flow in which you wish to encrypt data in the message payload, add an
encryption:encryptelement. -
Configure the element’s attributes and child element according to the tables below.
<encryption:encrypt config-ref="Encryption_PGP" doc:name="Encryption" using="PGP_ENCRYPTER" input-ref="#[message.payload]"> <encryption:pgp-encrypter principal="fernando.martinez <fernando.martinez@mulesoft.com>" /> </encryption:encrypt>Attribute Value config-ref
Required - Use the name of the global Encryption element you created.
doc:name
A display name for the element in Studio’s Visual Editor. Not applicable for Standalone.
using
Required - PGP_ENCRYPTER
input-ref
Enter a Mule expression to define the part(s) of the message Mule should encrypt. If this attribute is not defined, Mule encrypts the entire message payload.
-
Child Attribute: Required -
encryption:pgp-encrypter -
Child Element Attributes: Required - principal - An alternative to using a clientID and secret to authenticate a client, define a username and password as the principal.
-